Brute Force Password Cracker Osx
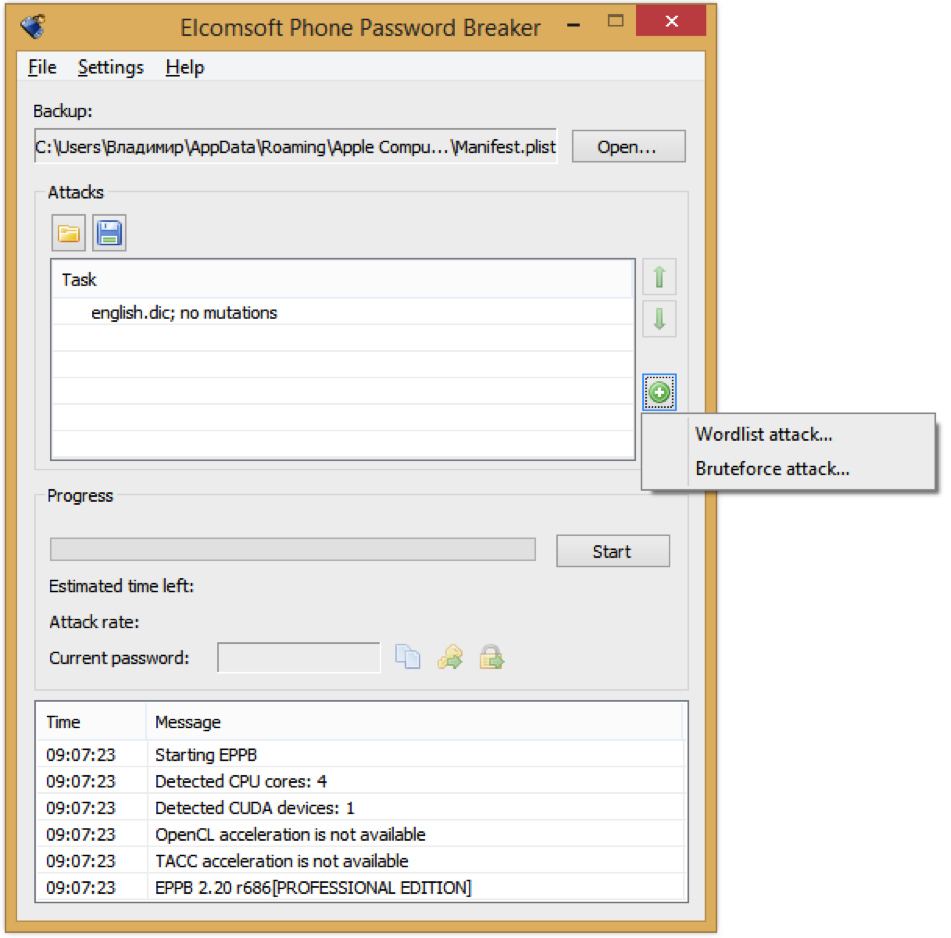
Brute force for mac free download. True Brute Force Tool This program works on everything that has a password. Takes 5 minutes to crack a 3 character.
A subreddit dedicated to hacking and hacking culture. What we are about: quality and constructive discussion about hacking and hacking culture.
We are not here to teach you the basics. Please visit for posting beginner links and tutorials. Hacking related politics welcome. Penalty table: Offense Penalty Spam/Clickbait Permanent ban. 'How to hack (x)/Help me hack (x)' type of questions 30 days ban. Aiding those who want help to hack anything 5 days ban Sharing private data (dumps etc.) 15 days ban Rules • WE ARE NOT YOUR PERSONAL ARMY • Questions and discussion prompts should be geared towards intermediate to advanced hackers.
• Requesting help/instructions on how to hack anything will be met with ridicule and a ban. Goemon Shin Sekai Shuumei more. Also, nobody cares if you got hacked.
Sorry, have a better password. Pinnacle Studio 14 Activation Key on this page. • Aiding those who are looking for help to hack anything will be banned. • Sharing Private data is forbidden (no IP dumping). • Spam is strictly forbidden and will result in a ban. (Spam as in links that violate the spam guidelines ) • Off-topic posts will be treated as spam. • Jail-breaking and rooting of phones and posts that aren't directly related to mobile security should be directed to other subreddits such as. • Off-topic or surly responses will be removed (a cryptographic hash!= potato hashes).
• Want to learn 'How to hack'?, Please head on to as questions about 'how to hack' anything aren't allowed here. IRC Note: if no one answers immediately, stick around and someone will read it. Recommended Subreddits: • • • • • • • • •.
I have my old macbook from a few years back, I don't remember the password exactly but I do recall some of the characters from my password at the time so I was thinking I could probably get the rest using a version of a script that's readily available. Warcraft 3 The Frozen Throne Patch 1.26 B. The problem is that when I test on a hash for 'password' with the string that's in the example I get a different value than the hash provided.
As such I'll never be able to get my old password. Here is the relevant code pulled from #Should be 8 characters of salt + sha hash for 'password' if I'm understanding this correctly digest = '33BA7C74C318F5D3EF40EB25E1C42F312ACF96' salt = '33BA7C74' sha1 = 'C318F5D3EF40EB25E1C42F312ACF96' try: salt_hex = chr(int(salt[0:2], 16)) + chr(int(salt[2:4], 16)) + chr(int(salt[4:6], 16)) + chr(int(salt[6:8], 16)) # CONVERT SALT TO HEX check('password', salt_hex, salt) def check(password,salt_hex, salt): # HASH PASS AND COMPARE if not password.startswith('#!' ): #IGNORE COMMENTS sha1_guess = hashlib.sha1(salt_hex+password).hexdigest() print('Trying with salt_hex ' + password) print sha1_guess.upper() print ' n' sha1_guess = hashlib.sha1(salt+password).hexdigest() print('Trying with salt ' + password) print sha1_guess.upper() print ' n' if sha1 in sha1_guess.upper(): print('Cleartext password is: '+password) exit(0) Unfortunately the output from both of these attempts is incorrect $ python sha_crack.py Attempting to crack. 33BA7C74C318F5D3EF40EB25E1C42F312ACF96 Trying with salt_hex password 9D8F0A15CF344F7FB35A1918AA0627 Trying with salt password E105192888CC1C34B7535AAA0425EC06F653A1B9 Article I was working from to test showing that this hash is for 'password'. The sample hash you're using is simply incorrect. If we take instead a test vector provided in, we'll see that code works as expected (correct password is ' macintosh' as per Wiki): import binascii import hashlib hash = '0E6A48F765D0FFFFF6247FA80D748E615F91DD0C7431E4D9' salt = binascii.unhexlify(hash[0:8]) sha1 = binascii.unhexlify(hash[8:]) passwords = ['123', 'password', 'macintosh'] for password in passwords: if hashlib.sha1(salt + password).digest() == sha1: print 'Password is '%s '% password break.